The digital transformation of energy, with its real-time monitoring and control systems, promises not only efficiency but also increased vulnerability. The CyberSEAS project aims to address this challenge by bolstering the resilience of energy supply chains against increasingly complex cyberattacks.
As digitalisation has sweeps across the energy sector, the ever-growing dependence on data in our smart grids creates a target for malicious actors, potentially causing widespread disruptions.
The CyberSEAS project (Cyber Securing Energy dAta Services)[1], led by Engineering, is focused on tackling the complex challenge of cyber resilience in Electrical Power and Energy Systems (EPES). With the increasing connectivity of data feeds, the presence of legacy systems, and the evolving nature of attack scenarios, and the expanding involvement of various stakeholders and consumers, safeguarding EPES demands a multifaceted approach.
The project has 3 strategic objectives:
- Countering the cyber risks related to highest impact attacks against EPES,
- Protecting consumers against personal data breaches and attacks, and
- Increasing the security of the Energy Common Data Space.
All three objectives are equally important since cyber-criminals are shifting tactics to favour multi-stage attacks in which stealing sensitive data is a precondition for the real attack and enables them to maximise damage and profits.
The growing vulnerability of digitised energy systems
The project represents the appropriate and necessary response to the very dynamic trend of changing tactics in cybercrime within the EPES context. Traditionally, infrastructure cyber-attacks would be direct attacks to the machinery and typically targeted control systems, while today the shift includes exploiting data sensitivity.
Threat actors, especially large ones such as nation states, also carry out complex attacks that leverage supply chain dependencies, and this trend continues to grow, as highlighted in the July 2020 analysis by the Atlantic Council. Likewise, with the transition to scenarios where users are proactively involved, prosumer data is becoming more and more sensitive.
An adaptable ecosystem of security solutions
To achieve these objectives, CyberSEAS delivers an open and extendable ecosystem of 30 customisable security solutions providing effective support for key activities, and in particular risk assessment, interaction with end devices, secure development and deployment, real-time security monitoring, skills improvement and awareness, certification, governance, and cooperation.
CyberSEAS solutions are validated through experimental campaigns consisting of 100+ attack scenarios, tested in three labs, six piloting infrastructures across six European countries.
Out of the 30 solutions, 20 will reach a high Technology Readiness Level (TRL) 8+, which places them in a very advanced “route to market” position.
A comprehensive toolset approach
CyberSEAS architecture proposes a comprehensive toolset approach to improve the cybersecurity level of sensitive EPES infrastructures. Through the strategic integration of complementary security-enhancing technologies, this architecture represents a significant advancement in safeguarding EPES integrity.
The foundation for this architecture lies in its alignment with the Reference Model of Open Distributed Processing (RMODP) standard, which has been selected to support the architecture definition.
The testing phase of the CyberSEAS solutions aims to identify the synergies among them, and how they can be integrated for a broader impact. Nevertheless, the definition of the most appropriate “route to market” process is substantiated by stakeholders’ engagement and the involvement of cyber security experts belonging to the Market Interest Group (MIG).
Collaborative detection and response
CyberSEAS focuses on early detection of attacks and collaborative approaches among operators, introduces cyber-defence measures that speed up this detection, thus enabling prompt reaction and effective remediation.
The security measures are also fully customisable to the different infrastructures, easing the adaptation and hence the level of precision of actions that are taken – while at the same time allowing the computation of the overall (i.e. supply chain level) evaluation of the cyber resilience level.
For instance, as part of the CyberSEAS toolset, the HEINDALL tool developed by Ikerlan is a vulnerability detection tool that is focused on identifying security vulnerabilities in a certain environment including devices, systems, and applications.
It scans the environment for known vulnerabilities or other weaknesses that could be exploited by an attacker. The tool then reports these vulnerabilities to the system administrator or security team, so that they can take steps to patch or remediate the vulnerabilities before they can be exploited by attackers.
While both vulnerability detection tools and attack detection tools are designed to improve the security of computer systems and networks, they serve different purposes.
The MIDA tool, developed by Guardtime, is a tool for software supply chain integrity protection and origin validation for EPES, which is able to combat high impact attacks such as compromised firmware updates of operational technology (OT) devices in the Distribution System Operator (DSO) system.
Within the project’s scope, the MIDA tool has already been successfully validated in the system of Estonian DSO Elektrilevi. During the validation, the DSO’s file management system received tampered OT firmware updates that could, in the real operational environment, cause a wide range of malfunctions to the devices. These errors could lead to, for example, outages in the electricity grid.
During the validation process, the MIDA tool performed the integrity verification on all uploaded files to the system, detecting the tampered files and removing them from the active processes.
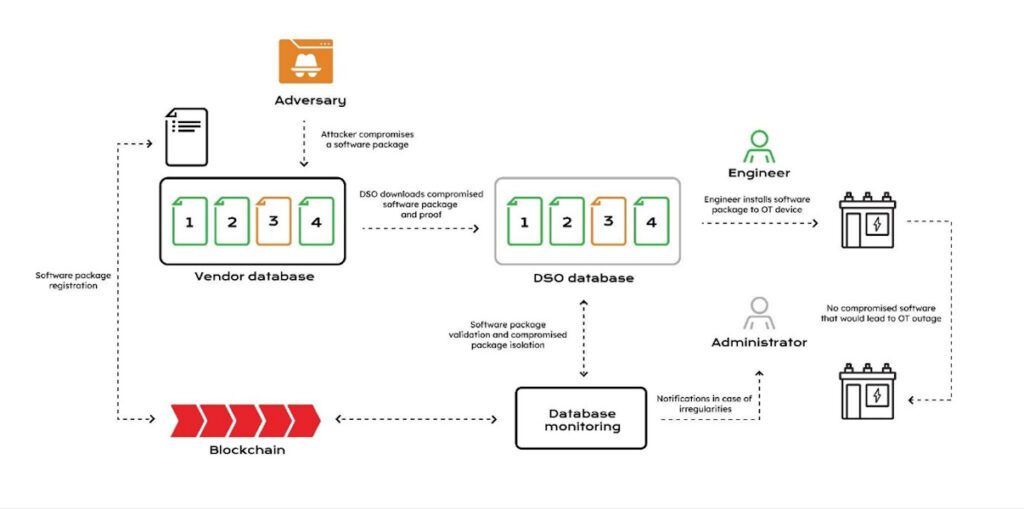
The MIDA tool is a quite relevant example of how CyberSEAS tools, among other aspects, support supply chain security risk mitigation, that has been highlighted in the NIS 2 directive.
The SecurGrid tool is implemented by project partner STAM. It aims to carry out a quantitative risk assessment of smart grid against cyber and physical threats. Thanks to the knowledge of the smart grid assets and of all the related components and services, it can model the grid’s infrastructure and produce a risk evaluation considering risk scenarios, related risk, and impact indicators.
SecurGrid is an independent model that, for the CyberSEAS project, is used as part of RATING-OT, the risk management solution developed by Engineering, and it can be used through its web application front-end.
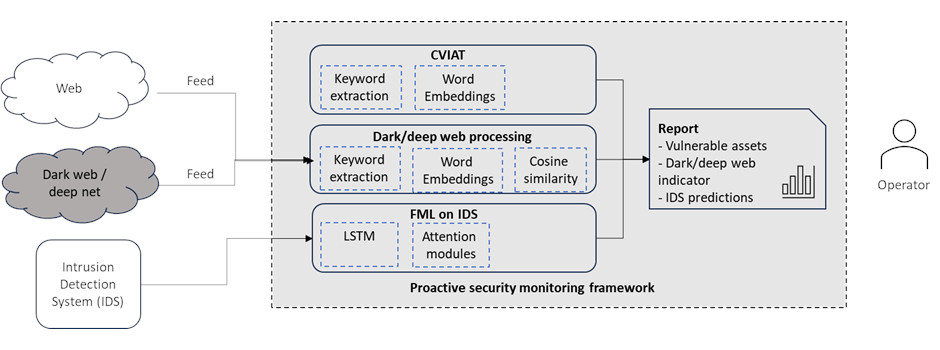
Further on, an example of effectively integrating three of the CyberSEAS tools under the umbrella of proactive cybersecurity notification, it is the solution developed by partner Synelixis. This is about energy operators receiving proactive cybersecurity notifications at the governance and the operational levels.
Regarding the former level (governance), CVIAT (Cybersecurity Identification and Assessment Tool), offers to the operators a wide pool of vulnerabilities potentially relevant to their assets [2]. This pool consists of more than 200 vulnerabilities stemming from NESCOR and NIST standards as well as previous risk analysis reports.
The operators select the vulnerabilities relevant to their assets and score them, using the CVSS scoring system.
CVIAT has been recently updated to support the recent CVSS4.0 scoring system. At the operational level, proactive notifications are retrieved from internal and external signals. The “FML on IDS” module monitors IDS packet logs and predicts, employing timeseries Machine Learning, the possibility of malicious packets (attack) in a configurable number of following packets. The component employs Federated ML techniques, and it has been recently enhanced to support Attention mechanisms.
In addition, the dark/deep web analysis module analyses (external) communications and texts (such as forum posts) from the dark and/or deep web and associates its part with vulnerabilities and metadata relevant to operators. The component employs keyword extraction and embedding (through RAKE and Universal Sentence Encoding libraries) [3]. The results from the three tools are combined in a weighted report, offered to the operator.
Addressing dynamic challenges in energy cybersecurity
The digitisation of energy is highly dynamic, and to the same extent are the challenges of cyber security. Moreover, the tactics and attacks in the sphere of cybercrime are becoming more and more creative and complex.
It is of particular importance that these movements can be anticipated, and that adequate, effective countermeasures are developed, especially in areas that have implications in critical infrastructure, such as the energy field.
About the Author:
Mihai A. Mladin is currently the Head of R&D&I department within Romanian Energy Center. Mihai has over 15 years experience in management consulting, EU funding and technical assistance projects, holding the positions of manager and senior consultant in a multinational, cross-industry environment. See Mihai’s full profile in the member’s directory
References
[1] CyberSEAS Project – Cyber Securing Energy dAta Services – Project under implementation, funded through the European Union’s Horizon 2020 program, Call: H2020-SU-DS-2018-2019-2020 – Digital Security, Proposal ID 101020560.
[2] Nikolaou, N.; Papadakis, A.; Psychogyios, K.; Zahariadis, T. Vulnerability Identification and Assessment for Critical Infrastructures in the Energy Sector. Electronics 2023, 12, 3185.
[3] Psychogyios, K., Bourou, S., Papadakis, A., Nikolaou, N., Zahariadis, T. (2023). Time-Series Modeling for Intrusion Detection Systems. In: Ossowski, S., Sitek, P., Analide, C., Marreiros, G., Chamoso, P., Rodríguez, S. (eds) Distributed Computing and Artificial Intelligence, 20th International Conference. DCAI 2023. Lecture Notes in Networks and Systems, vol 740. Springer, Cham.